News & Media
Podcasts
News
You are not alone. Join a peer group
Join our President and Founder, Dan Gilligan on one of his morning walks as he discusses how joining a peer group changed him for the better and why he thinks you need to join one.
How to Catch a Phish
👉 Follow Dan on LinkedIn: https://www.linkedin.com/in/dangillig… For more information about IntegraMSP and our services, Contact us today. 👉 Visit us at: https://integramsp.com Connect with us on our social media! 👉 IntegraMSP’s YouTube: / @integramsp9252 👉 IntegraMSP’s LinkedIn: https://www.linkedin.com/company/inte… 👉 IntegraMSP’s Twitter: https://twitter.com/IntegraMSP 👉 IntegraMSP’s Facebook: https://www.facebook.com/integramsp/ 👉 Schedule a free 30-minute consultation to see if…
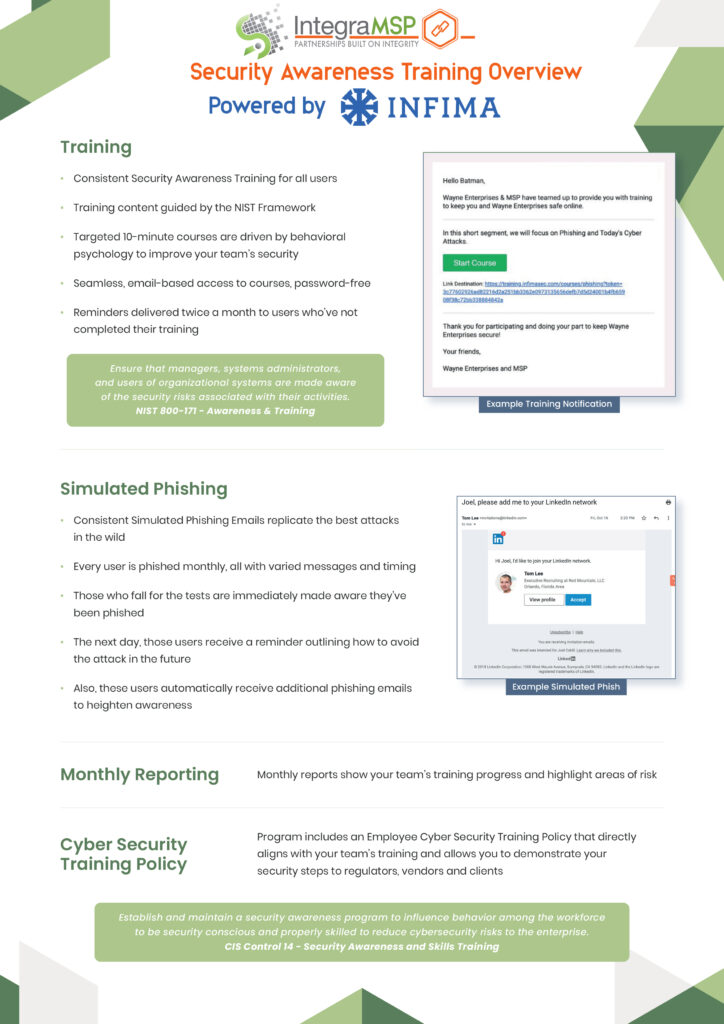
Does your MSP provide ongoing Security Training?
We Provide Security Awareness Training for your team – but what does that mean? What that means is IntegraMSP has partnered with Infima to provide best-in-class cyber security training. Using AI technology, Infima Security offers comprehensive security awareness training programs designed to educate employees and help your team prevent cyber attacks. These training programs cover…
Welcome to our newest team members!
We would like to welcome you to our newest team members, Alex Dang and Bryan Shanafelt. We are excited to have both on board with our team and we look forward to you getting to meet them!
Urgent Security Alert: Microsoft 365 Apps Vulnerability
We want to inform you of a critical security issue affecting Microsoft Outlook/365 applications. This vulnerability, known as CVE-2023-23397, is being exploited by cybercriminals and requires immediate attention. In simple terms, attackers can gain unauthorized access to your systems and steal sensitive information just by sending a specially crafted email. The concerning part is that…
Winning the Unfair Fight – Cyber Security for Small Business
Do you feel like it is almost impossible to get in front of the ‘cyber bad guys’ that are working to undermine your company? Does ransomware, phishing, man-in-the-middle attacks and more keep you up at night? Well – we invite you to our informative Webinar – ‘Winning the Unfair Fight – Cyber Security…
Are You Covered?
We had a nice long talk with our Cyber Insurance agent recently – and what we learned WILL directly impact small businesses with MSP Services. Did you know that if your Cyber Insurance Policy does not list your IT provider as a first line of defense in a cyber incident – then they shouldn’t be…
Cybersecurity’s WEAKEST link
As you may have heard – it is cybersecurity awareness month. While ‘kitchy’ – cybersecurity awareness should be a continuous, ongoing event – not just the month of October. And of course – we all know what the ‘weakest link’ is right? It’s Phil in accounting – isn’t it? No matter what amazing tools you…
You NEED a Password Manager – Yesterday
With cyberthreats on the rise – if you DON’T have a Password Manager – you need one ASAP. The days of passwords written on sticky notes or notepads are long gone. A secure, robust password manager is the best way to stay secure online. And bonus – you can have it on all of your…